
How does eKYC process look like?
An eKYC method refers to the workflow of how certain technologies are employed, while eKYC outlines the technology that banks use to authenticate online applications. A clear eKYC procedure is essential since it offers banks a complete picture of the onboarding process for clients. SmartOSC intends to examine a tried-and-true 10-step ekyc process in this article.
Internet form
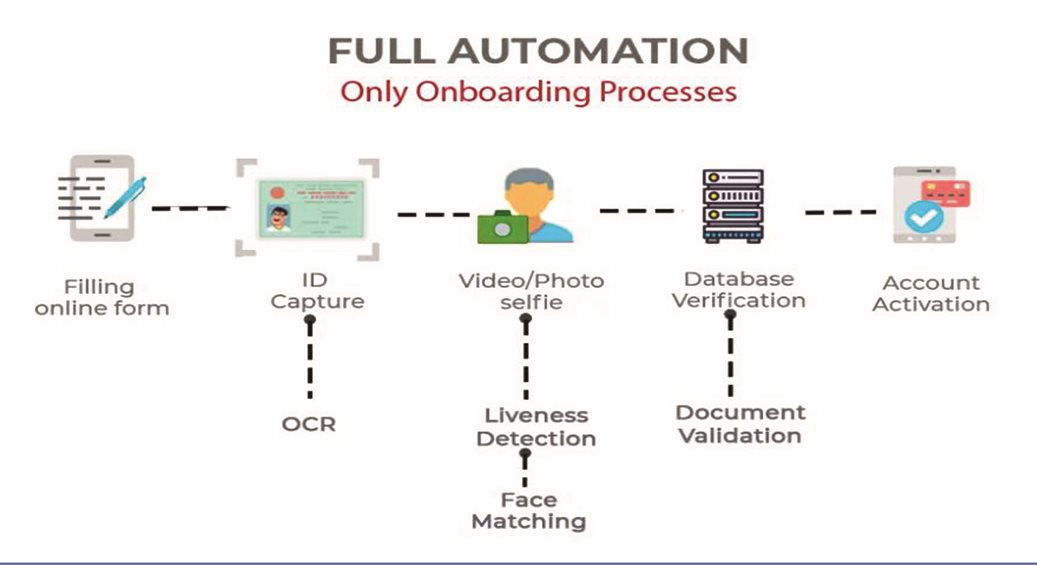
Forms that request users’ PII (Personal Identifiable Information) is shown at this first step of the ekyc process.
While many banks may request various personal information from customers, the following are some crucial ones:
- Name
- Address
- Date of Birth
- Telephone
- Security benefits
An eKYC system should provide form customization, allowing banks to change, add, or delete input fields as necessary to meet their requirements.
Using two factors to authenticate
SMS is the most often used method of two-factor authentication for the ekyc process. Two-factor authentication works as follows in an eKYC:
- Individuals key in their phone number
- Customers get an automated one-time password on their phones
- Customers find the password and input it into their smartphone app.
Even though it is not a legislative necessity, two-factor authentication is often used in modern eKYC (and adding it to the eKYC procedures sure can increase attrition). However, if banks are to verify users’ legitimacy and thwart fraud efforts.
Smartosc solutions : BACKBASE DIGITAL BANKING, BUY NOW PAY LATER, LOS, CDP, EKYC, DIGITAL ONBOARDING
Taking IDs
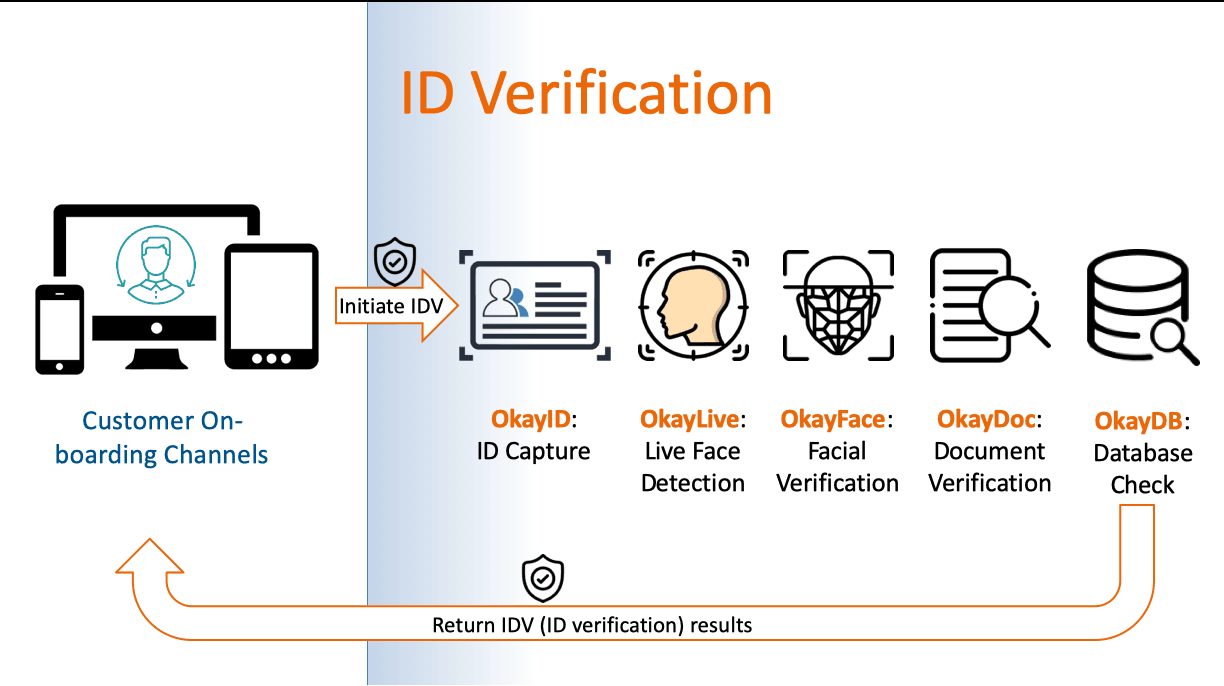
The front and back of users’ identification papers, such as ID cards, passports, and licenses, must be photographed.
One of ID Capture’s best practices for the ekyc process is to provide users with background information and guidelines. For instance, a straightforward request like “please place the face of your ID card into the frame” would be appropriate.
OCR (Optical Character Recognition), a machine learning tool that can extract data from the ID papers, powers ID capture.
Authentication of identity

This ekyc process enables banks to determine if the application and the person listed on the paperwork are the same. Identity verification in an eKYC procedure often includes face matching and liveness detection.
These eKYC procedures could be perplexing to new users. Face matching and liveness detection are simple tasks that novice users often struggle with. Frustration is inevitable when they are made to do these verifications over and again.
Database audit
To confirm the applicant’s legal existence, the eKYC procedure pings all third-party databases, including CIC, Personal Income Tax, and Social Security.
The eKYC method becomes more efficient at confirming users’ identities as more databases are connected with it.
Detecting fraud

Built-in ML algorithms assess common signs of fraud (such suspicious IP addresses, email addresses, or even how quickly people fill out the form).
The fourth phase is taking place in the background, so users cannot see it. Users are often informed that their information is being processed via a message.
AML Detection
Data and photos given by users are checked against politically exposed person lists and watchlists published by the government. Because it assures adherence to anti-money laundering (AML) rules and procedures as needed by regulators, this phase is crucial to the ekyc process.
Enhanced Due Diligence

For high-risk consumers, this phase requires more documentation and/or enhanced due diligence (or “EDD”) inspections. Users must, for instance, provide evidence of address, such as a copy of a utility bill or bank statement.
Threat pools
Users are assigned to appropriate risk pools based on all of the ekyc processes that have already been conducted. High-risk individuals are separated and manually assessed in the interim.
Ongoing observation
After the consumers have been onboarded, the eKYC procedure does not finish. Users are continually watched after they have an account. AML and behavioral surveillance are part of this phase (anomaly detection).
It should be noted that the aforementioned ekyc process is far from universal. Some procedures may be omitted depending on the items that banks provide. Banks may do without two-factor authentication and more thorough due diligence for low-risk items like children’s prepared cards. We appreciate your reading. If you want to learn more, get in touch with SmartOSC.


